The ABC of Azure Roles and Role based Access Control
Azure Roles & Role Based Access Control (RBAC)
Introduction
This concept even though very simple, yet becomes complex if
we get confused with basics. My early days, I studied this chapter from Azure docs many times to understand the
intricacies of roles and RBAC. With years passing by I started getting an understanding of how
important Roles and RBAC is!
Today I am going to share my views and thoughts on roles and
role based access control by presenting a usecase with you. The blog will
present the case, explain the concept and relate it to the usecase presented.
Once we complete the usecase I would like you to take an
assignment which I have attached below
Finally a bit long blog, so please relax and digest the
concepts. Besides please remember this is one of key topics in every azure
certifications.
Usecase
Sara, a young entrepreneur running “S5 Enterprise”. Sara is
planning to launch 2 business applications “S5 Retail” and “S5 Pharma” partnering
with SaanV and Gita respectively.
With the cloud revolution in place, Sara is planning to host
applications on Azure. Sara hired different professionals to support her in
building applications to support her
Sara believes in understanding things before she applies.
Besides Sara had gone through fundamentals of Azure before she decided to
launch application. Sara understand that users need to be given least privilege
to perform their functions. She wants to implement Best practices while building
their solution on Azure.
Sara converses with Srikanth Kappagantula, an Azure
Administrator to understand Azure specifics in terms of Accounts,
Subscriptions, and Tenants while setting up Azure Account. The team includes -
- Business Partners
- SaanV, Partner “S5 Retail”
- Gita, , Partner “S5 Pharma”
- Internal Team
- Srikanth Kappagantula, Azure Administrator
- Srini, User Admin
- Shaila, Accounting
- Nara, Administrator
- JC, User Access Administrator
- Lucky, Internal Auditor
- External Teams
- Sailesh, External Auditor
- Development Team, Development Partners
- Operations Team, Managed Services Partners
 |
| Sara Team |
Let's look at fundamentals
What is a Role/Role Definition?
Role/Role definition is collection of permissions on objects in a namespace. Generally a Role has a unique name and a description with collection of permissions. A role definition is assigned to Security Principals (Users, Groups, Service Principals, and Managed Identities) allowing them to perform the operations such as read, write, and delete on objects in a namespace.
Every security principal is allocated to ROLES with LEAST PREVILEGE which allows them to perform or not perform certain Actions.
Besides, LEAST PREVILEGE defines ability to
perform/not perform specific Actions at mentioned SCOPE. Not More Not Less
What is SCOPE
Scope is the set of resources that the access applies to and
when a role is assigned, we can further limit the actions allowed by defining a
scope. To understand scope, let us define some common terms we use across the
solution.
Azure Account
- A Global Unique Entity
- Can be an Individual Account or an
Organization Account
- Account contains multiple
subscriptions & active directory tenants
- Organization is Business Entity and
identified by one/more public DNS domain names
Azure
Active Directory Tenant
- Representation of an organization
- Unique instance of Azure Active
Directory
- Tenant has its own identities, and
app registrations
- Azure Active Directory Tenant can
have more than 1 subscription
Management
Groups
- Management groups are containers to
manage access, policy, and compliance for multiple subscriptions
- Subscriptions in a management group
automatically inherit the conditions
Subscription
- Agreement with Microsoft to use Microsoft cloud platforms or services
- Billing Relationship between Party
and Azure
- Can host resource groups (resource
containers) & Resources
- 1 Subscription can be allocated to
only 1 Active Directory Tenant
Resource
Group
- Resource Group is logical container
for Resources
- Subscription can have 1 or more
resource groups
- 1 Resource Group can be allocated
only to one subscription
- Resource Group stores its metadata
in a location
Resource
- Resources are instances of azure
services for e.g. virtual machines, storage, or SQL databases
- A Resource can be assigned to only
one resource group
- Location of a resource can be
different from location of a resource group
- Each Account can have 1 or more Azure Active Directory Tenant and subscriptions
- Each Azure Active Directory Tenant can be linked to more than 1 subscription while converse is not true
- Each Organization can have multiple Management Groups
- Each Management Group can have more than 1 subscription
- Each subscription can have more than 1 resource group
- Each resource group can have more than 1 resource
Roles are defined at a pre-defined scope or roles will be allocated at a specific scope
Types of Roles in Azure
There are 3 types of roles in Azure that can be assigned at
a scope
- Classic Subscription Administrator roles
- Azure Active Directory Tenant Roles
- Azure Roles (based on RBAC)
Classic Subscription Administrator roles
Classic Subscription roles are applied at Azure account
level. These roles deal with management of Account and configuration of their
Active Directory Tenant(s) and Subscription(s). Mostly these roles are managed
by user/organization who creates the account. They nominate other users to
manage the account to handle specific functions. These roles comes with
unlimited access. Be very cautious when you assign this role to a user
These roles are built and only managed by Microsoft. We can create custom role(s) at this level.
- Have full access to Azure Accounts & Subscriptions
- Can manage resources using Portal & ARM API’s
- Created when Azure Account is created
The Built-in Roles in Classic Administrator roles includes
- Account Administrator
- Service Administrator
- Co-Administrator
Azure Active Directory Tenant roles
Azure Active Directory Tenant roles as name suggests, are
related to Azure Active Directory Tenant. These roles have full/unlimited
access to AD objects and properties tagged to role identified. Mostly 2-3 roles
are mostly used if we are dealing only with Azure. In case, we are even opting
for Microsoft 365, then more number of roles need to be used to manage
functions.
At Active Directory Tenant level, you can create custom roles that span across multiple objects. Only Active Directory P1 and Active Directory P2 supports creating custom roles
- Used to manage Azure AD resources in a directory
- Perform different functions
- User management
- License management
- Manage domains
The key built-in roles related to azure includes
- Global Administrator
- User Administrator
- Billing Administrator
Azure roles
These roles are based on Role based access control (RBAC).
These can be applied to Management Group(s) -> Subscription(s) ->
Resource Group(s) -> Resource(s). The roles exhibit inheritance in relation
to scope and when applied at a scope, the role access automatically applies the
same to child scope. The role at a scope carries additive nature to child
scope(s).
- Based on Role based access control
- Authorization system that provides fine grained access to azure resources
- Has 4 fundamental roles and 70 built-in roles
- Owner
- Contributor
- Reader
- User Access Administrator
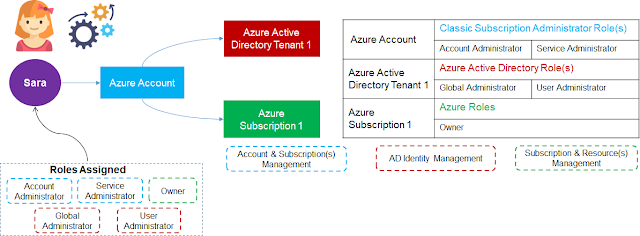
Sara created her Account and Srikanth explains what happens next
When Sara creates her Azure Account, one Azure Active
Directory Tenant and a subscription are created. Along with this, couple of
roles from the above mentioned roles are allocated to her which includes
Azure Account & Subscription Management
o
Account Administrator
o
Service Administrator
·
Azure Active Directory Tenant Management
o
Global Administrator
o
User Administrator
·
Subscription & Resource Management
o Owner
- Azure Active Directory (AAD) tenant 1 and a subscription 1 created post account creation
- AAD is identity management solution. More than 1 AAD tenant instance can be created later
- Subscription is the billing relationship between azure and Sara.
- More than 1 subscription can be created if you want to segregate billing for different applications
- 1 AAD tenant can be linked to many subscriptions
- 1 subscription can be linked to only one tenant
- An Account can have multiple Active Directory tenants and Subscriptions
Sara was quite excited with the Azure Account creation
process and interested to know more about different roles and types of roles
created.
Classic Subscription Administrator Roles
Classic Subscription
Administrator roles have full
access to the Azure subscription & Account. These roles can manage
resources using Portal & ARM API’s. These roles are created when Azure
Account is created
There are 3 types of classic subscription
administrator roles
q Account
Administrator
q Service
Administrator
q Co-Administrator
Account Administrator
There can be Maximum 1 Account
Administrator per Azure Account. Most Powerful role in an Account. The role can
manage (create/cancel) all subscriptions and azure active directory tenants in
Account. Also the role can manage & change billing for subscriptions.
Specifically the role can change the Service Administrator
Service Administrator
There can be maximum 1 per
Azure Subscription. This role can manage services in azure subscription and
also can cancel subscription. This role can assign users to Co-Administrator
role and also associate a subscription to a different Active directory tenant
Co-Administrator
Srikanth cautioned Sara about usage of these roles
- Classic Administrator Roles comes with unlimited access to accounts and subscriptions and suggested the following best practices
- Assess the need for the role before you assign it to a user
- Service Administrator role can change the Active Directory domain or even add new AD Tenant
- Service Administrator can cancel subscriptions without Account Administrator involvement
- Service Administrator can order services/resources on subscription
- The number of Co-Administrators should not be more than 1 or 2 per subscription
- Limit the permissions of co-administrators on specific subscription resources through Deny Assignments
Sara asked Srikanth to create the following Account Management roles
- “S5 Retail” with SaanV
- “S5 Pharma” with Gita
- SaanV “Service Administrator” to subscription “S5 Retail”
- Gita “Co-Administrator” to Subscription “S5 Pharma”
- Srikanth a Co-Administrator to both Subscriptions, Temporarily (to manage subscriptions temporarily)
Azure Active Directory Roles
Azure Active Directory is Microsoft’s cloud-based identity and access management service to manage
q External Resources
q Microsoft 365,
q The Azure portal,
q Other SaaS applications
q Internal resources
q Apps on your corporate network
q Apps on intranet
q Cloud apps developed by your own
organization
Azure Active Directory roles are used to manage Azure AD
resources in a directory. Different functions include-
· 1. User Management
· 2. License Management
· 3. Domain Management
Some of the key roles related to Azure administration
includes –
· 1. Global Administrator
· 2. User Administrator
· 3. Billing Administrator
We have other built-in roles defined in Azure AD related to
other AD objects
Global Administrator
Global Administrator is assigned to the person who creates
azure Account by default. Global Administrator when assigned to a user can manage
Active Directory objects. The role handles access to admin features in Active
Directory. This role can assign administrator roles to other users as well as
reset password for users
User Administrator
User Administrator can create
& manage users, manage support tickets, manage service health and change
password for users. This role is mainly assigned to user who handle user
management and also manage operations tickets and work with Microsoft to solve
issues
Billing Administrator
Billing Administrator is responsible to make purchases,
manage subscriptions, service tickets and service health. The user who has been
assigned this role can manage all the subscriptions in terms of ordering new
services and billing services
Other Built-in Administrator roles
·
Application Administrator
·
Application developer
·
Azure Devops administrator
·
….
Azure Active Directory Roles are specifically related to
management of Active Directory objects and support different functions that can
be set at directory level
Srikanth re-iterated more about Global Administrator
Sara was quite fascinated about Global Administrator role
and wanted to know more about it. Srikanth explained – as pervious said, Global
Administrator works with Azure Active Directory and its objects but again this
role comes with unlimited access on Azure Active Directory, you need to grant
this role to a very small group of people.
Many times, Global Administrator may not have access all
subscriptions and management groups even though they manage the Active
Directory partially because the subscriptions are not allocated to that Active
Directory.
There may be situation where we need to
· Regain access to an Azure subscription or management group which a user has lost access
· Grant another user or yourself access to an Azure subscription or management group
· See all Azure subscriptions or management groups in an organization
· Allow an automation app (such as an invoicing or auditing app) to access all Azure subscriptions or management groups
We can elevate access of Global Administrator to manage all subscriptions and management groups. But this activity need to be performed only as a backup plan or emergency plan.
We can elevate the access of Global Administrator by
toggling on elevate access in Active Directory properties. This will enable
User Access Administrator permissions at root level. All management groups and
subscriptions are granted access to Global Administrator.
Once you complete the activity, then toggle off the elevated
access.
Sara asked Srikanth to create the following roles
Sara sees a need to manage the following functions
Manage Billing centrally
Create/Drop Users to a single AD domain
Administrator to manage AD end to end
Sara advised Srikanth to make Srini User Administrator, Shaila Billing Administrator and Srikanth, the Global Administrator role.
Can you appreciate Sara’s decision with respect to Shaila. If Yes, Why?
Custom Roles in Azure Active Directory
Sara asked Srikanth, is there a way I can pick up different
functions from different roles keeping least privilege in mind and assign
access to only specific functions.
Srikanth replied, “Indeed, You can”. We can define
custom roles to define the custom roles where we can define multiple functions
like managing apps, viewing bills, etc. But to create custom roles, Active
Directory instance should have a minimum of Azure AD Premium P1 level
configuration.
Custom roles will have 3 parameters
-
Security Principal
-
Role Assignment
-
Scope
Sara asserts, I will come back to you on this. Besides,
please explain Azure Roles.
Srikanth assures the role structures in Azure AD and Azure
are same and elaborates Azure Roles.
Azure Roles
Azure Roles are based on RBAC (Role based access control)
mechanism. These roles are designed to manage azure subscription resource
groups and resources
There are 4 types of built-in roles
·
Owner – Owner role has full access to resources.
The owner role can delegate access to others
·
Contributor – Contributor role can create and
manage azure resources, can create new azure tenant while cannot grant access
to others
·
Reader – Reader role can view all the resources
for a scope
·
User Access Administrator – user access administrator
can manage access to azure resources
Sara interrupted, Are these the only roles we have in
Azure roles?
Obviously No. Some of the azure built-in roles are defined
at resource types. For e.g.
-
Virtual Machine contributor
-
Storage Data Owner
-
Storage Account Reader
-
Network Contributor
-
Backup Operator
-
…
Sara quizzed Srikanth with couple of questions
1.
How can I enable multiple functions to a user
for e.g. create and manage all storage accounts and view all virtual machines
2.
How can I enable multiple functions at multiple
levels to a user for e.g. create and manage specific blob storages in storage
accounts, manage specific virtual machine instances, edit virtual networks
assigned to him
Srikanth replied “These are 2 unique problems with 2
different solutions.
The first solution is simple “configure multiple roles at
specific resource types” to a user. This will allow the user to perform the
functions at multiple resource types. For the above problem we assign “Storage
Account Contributor” and “Virtual Machine Reader” to users/groups
For second problem, Azure built-in roles cannot fulfil this
requirement. We need to build “Custom roles” to address this requirement. Custom
Roles are user defined roles with specific Actions, Data Actions, NotActions
and Not Data Actions at a defined scope
Sara interrupted, this topic looks more confusing hearing
new terms like Actions, Data actions and asked for more explanation. Srikanth
replied, Let me explain you what is “role based access control” and then
explain you the dependent topics in detail
What is Role based Access Control
Azure role based access control (RBAC) in Azure defines the
approach to manage access control on cloud resources to identities. Before we
jump into more details, we need to answer 3 basic questions
·
Who has access to an azure resource?
·
What can they do with those resources?
·
What specific areas they need to have access to?
Azure Role based access control (RBAC) is an authorization
system built on Azure Resource Manager (ARM) which provides fine grained access
to azure resources. For e.g.
·
DBA Group to manage SQL and NOSQL
databases
·
Network administrator to manage Virtual
Networks
·
Application Administrator to manage App
Services
·
Project Administrator to manage resources
in a resource group
·
Storage Admin to manage storage accounts
Let us understand how RBAC is implemented. Basically in
Azure, RBAC is implemented through:
·
Role Definitions - Role definition
(typically a role) is a collection of permissions. Supports operations
like create, view, update and delete
·
Role Assignments - Manage Access to
different azure resources at a specific scope is enabled by role assignment
·
Deny Assignments - Deny Access to
different azure resources at a specific scope is enabled by deny assignment
·
Custom Roles - Custom Roles are created when built-in roles
cannot fulfill the purpose
Let me explain concepts in detail
What are Role Definitions
A role definition (typically a role) is a
collection of permissions. A
role definition lists the operations that can be performed, such as read,
write, and delete.
Basically
we have 2 types of roles
· Built-in Roles – Built-in Roles are
defined by Azure. Built-in Roles are of 2 types
o
High
Level – Roles with full permissions at a scope
o
Resource
Specific Type – Roles with specific permissions for a specific type at specific
scope
·
Custom Roles – Custom Roles are created when built-in roles cannot fulfill
the purpose. Custom Roles are user defined roles which define different
access mechanisms to different Resource Specific Types for specific Actions
Operations are of 2 types –
·
Management Actions control access to resources
for e.g. access storage account, create, update and delete blob container,
delete resource group & its resources
·
Data Actions control access to data underlying
resources for e.g. read log files in blob container, delete a message in a
queue, write data into text file in a container
Role Definition has 7 components
·
Name – Name of the roles
·
ID – ID for the role
·
IsCustom – Whether the role is a built-in role
or custom role created
·
Description – Purpose of the role
·
Actions - Management operations that the role
allows to be performed. For e.g. Storage Blob Reader role definition, which
includes operations in the Actions properties. This role allows you to read the
blob container. It is not allowed to read underlying data
·
NotActions - Management operations that are
excluded from the allowed Actions
·
DataActions - Data operations that the role
allows to be performed to your data within that object. For e.g. Storage Blob
Data Reader role definition, which includes operations in both the Actions and
DataActions properties. This role allows you to read the blob container and
also the underlying blob data
·
NotDataActions - Data operations that are excluded from the
allowed DataActions
·
AssignableScopes - Scope the role is available
for assignment. For e.g. Management Group/Subscription/Resource Group/Resource
Let us look at an example
{
"Name":
"Virtual Machine Operator",
"Id":
"88888888-8888-8888-8888-888888888888",
"IsCustom": true,
"Description": "Can monitor and restart virtual
machines.",
"Actions":
[
"Microsoft.Storage/*/read",
"Microsoft.Network/*/read",
"Microsoft.Compute/*/read",
"Microsoft.Compute/virtualMachines/start/action",
"Microsoft.Compute/virtualMachines/restart/action",
"Microsoft.Authorization/*/read",
"Microsoft.ResourceHealth/availabilityStatuses/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Insights/alertRules/*",
"Microsoft.Insights/diagnosticSettings/*",
"Microsoft.Support/*"
],
"NotActions": [],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": [
"/subscriptions/{subscriptionId1}",
"/subscriptions/{subscriptionId2}",
"/providers/Microsoft.Management/managementGroups/{groupId1}"
]
}
What are Role Assignments
Role Assignments control access using roles to security
principals at a specific scope. Role Assignment has 3 components
-
Security Principal (Identity that requests
access to an azure resource)
-
Role Definition (Collection of permissions)
-
Scope (set of resources that the access applies to)
Security Principal - security principal is azure object that represents a user, group, service
principal, or managed identity that is requesting access to Azure resources.
There are 4
types of Security Principals
· User – individual who has a profile
in Azure Active Directory
· Group – Group, to host set of users
created in Azure Active Directory
· Service Principal - security
identity used by applications/services to access specific Azure resources
·
Managed
Identity - identity in Azure Active Directory that is automatically managed by
Azure
Role definition – collection of permissions
Scope -
The set of resources that the access applies to. Assign a role, and limit
the actions allowed by defining a scope. Scope is additive, for e.g. access
granted at subscription flows down to resource group and thereby to resources
Scope can be defined at 4 levels
·
Management Groups - Each Management Group can
have 1 or more subscriptions
·
Subscriptions - Each Subscription is a
collection of 0 or more resource groups
·
Resource Groups - Each Resource Group is a
collection of 0 or more resources and resource types
·
Resources - Resource is smallest unit in the
scope
Let me explain the definitions in detail
·
Management Groups - Management groups are
containers to manage access, policy, and compliance across multiple
subscriptions. Management Groups enable an effective and efficient hierarchy
that can be used with Azure Policy and RBAC Controls. All subscriptions in a
management group automatically inherit the conditions applied to the management
group
·
Subscriptions - A subscription logically associates user
accounts and the resources that were created by them. Organizations use
subscriptions to manage costs and the resources that are created by users,
teams, or projects.
·
Resource Groups - Resource group is a logical container into
which Azure resources like Services, databases, web apps, and storage accounts
are deployed and managed.
·
Resources - Resources are different services that we create in azure. For e.g. Containers, SQL Databases, Web Apps, Storage
Accounts
What are Deny Assignments
Deny Assignments are set of Deny Actions assigned to a
security principal at a specific scope. Similar to Role Assignments, Deny
Assignments have 3 elements
-
Security Principal (Identity that requests
access to an azure resource)
-
Role Definition (Collection of permissions)
-
Scope (set of resources that the access applies to)
Deny Assignments prevents
security principals to prevent performing actions at a scope even Role
assignments are defined at one level above. Deny Assignments can be created
only with Azure Blueprints and Azure managed Apps.
Sara interrupted
Srikanth, with a question
At a Specific Scope
(Management Groups/Subscriptions/Resource Groups/Resources), what will take
precedence when both Role Assignment and Deny Assignment are defined?
Srikanth advised that
RBAC always works with a role with limited access to perform an action. At a Scope, Deny Assignment always takes
precedence over Role Assignment
Creating roles at RBAC level
Sara laid out the
requirements for role based access control and asked srikanth to assign roles
· Srikanth to oversee and manage administration
across both subscriptions
· Nara need to be able to create and drop services
· JC to handle User Access for services for both
subscriptions and Storage Management
· Lucky and Sailesh need to address Auditing
· Implementation of Services outsourced to
Development Partners
· Operations outsourced to Manage Services partners
Srikanth created roles
for the following users
· Srikanth is assigned owner role at both
subscription levels S5 Retail and S5 Pharma
· Nara is assigned Contributor role at both
subscription levels
· JC is assigned User Access Administrator, Storage
Account Contributor
· Lucky & Sailesh are given Reader role at
subscription levels
Regarding 2 roles
pertaining to Development Partners and Manage Services partners, Srikanth
advised Sara to allow allocating resource specific type and custom roles for access
on specific resource instances
Srikanth elaborated about
resource specific types of roles
· When permissions need to be granted to specific
resource types in any scope, use resource specific roles
· For e.g. for Storage you have role to support
Actions and Data Actions
· Storage Account Types and specific roles defined
in diagram –
§ Blob
§ File
§ Queue
Srikanth asserts 2 considerations
·
Implementation Services Team will have to access
multiple services like storage, Virtual Machines, administration, monitoring,
and management
·
Operations team need to monitor and manage
different services and even need to perform fixes and other support activities
Upon agreement with Sara, Srikanth move forward by
q Creating
Groups of Users and assign multiple roles which provides Data Actions and
Actions at a specific scope
q Creating
Groups and assign CUSTOM Roles which span across multiple services
Also Srikanth re-iterated the importance of custom roles
q Sometimes Azure Built-in roles does
not serve the specific needs of your organization. Create custom roles to
address the specific requirement
q Custom Roles are user define roles
with specific Actions, Data Actions, NotActions and Not Data Actions at a
defined scope
q Custom roles can be shared between
subscriptions that trust the same Azure AD directory
q Custom Roles can be created using
Azure Powershell, Azure Portal, Azure CLI or Rest API
It is easy to create an azure custom role through portal using “clone a role” option. The following custom roles are created
Sara’s concerns about subscriptions and active directory
• What
happens when one subscription is moved from Active Directory Tenant 1 to Active
Directory Tenant 2? She raised the concern if there may be a need to separate
one of the subscriptions under a new domain
• How
to determine if a user has access to specific role in Azure Active Directory or
Azure
• How
can we address audit requirements
Srikanth explains
What happens when one subscription is moved from Active
Directory Tenant to other
When a subscription is moved from 1 active directory tenant
to other-
q Roles
Assignments are permanently deleted
q Map
Security Principals to corresponding objects in new AD Tenant
q
Recreate Role Assignments
q Custom
Roles are permanently deleted
q
Recreate custom roles and role assignments
How to determine if a user has access to specific role in
Azure Active Directory and Azure roles
The access validation process is almost similar in both
active directory and azure.
For Azure Active Directory, check for assigned roles for a
specific security principal
While for azure roles, click subscription. In IAM tab, check
access
How do we address audit requirements?
To track changes with respect to auditing, especially
-
Create role assignment
-
Delete role assignment
-
Create or update custom role definition
-
Delete custom role definition
Srikanth explains Activity Log logs all the activities to
support auditing and troubleshooting purposes
q Changes
in role assignments, custom role definitions and activities are tracked
q Hosts
the log data for 90 days
Conclusion
Sara looks contented with Srikanth, the way whole process
went and quite happy working with Srikanth. She scheduled another meeting with
Srikanth coming Tuesday, to discuss identity management more from Srikanth, the
administrator perspective.
Srikanth exclaimed and said, well I am looking forward for
the meeting. Besides, I would share the slides of our discussion and drop you a
small assignment to know how well you understood the concepts discussed. Sara
happily nodded and left for her next meeting.
















Comments
Post a Comment